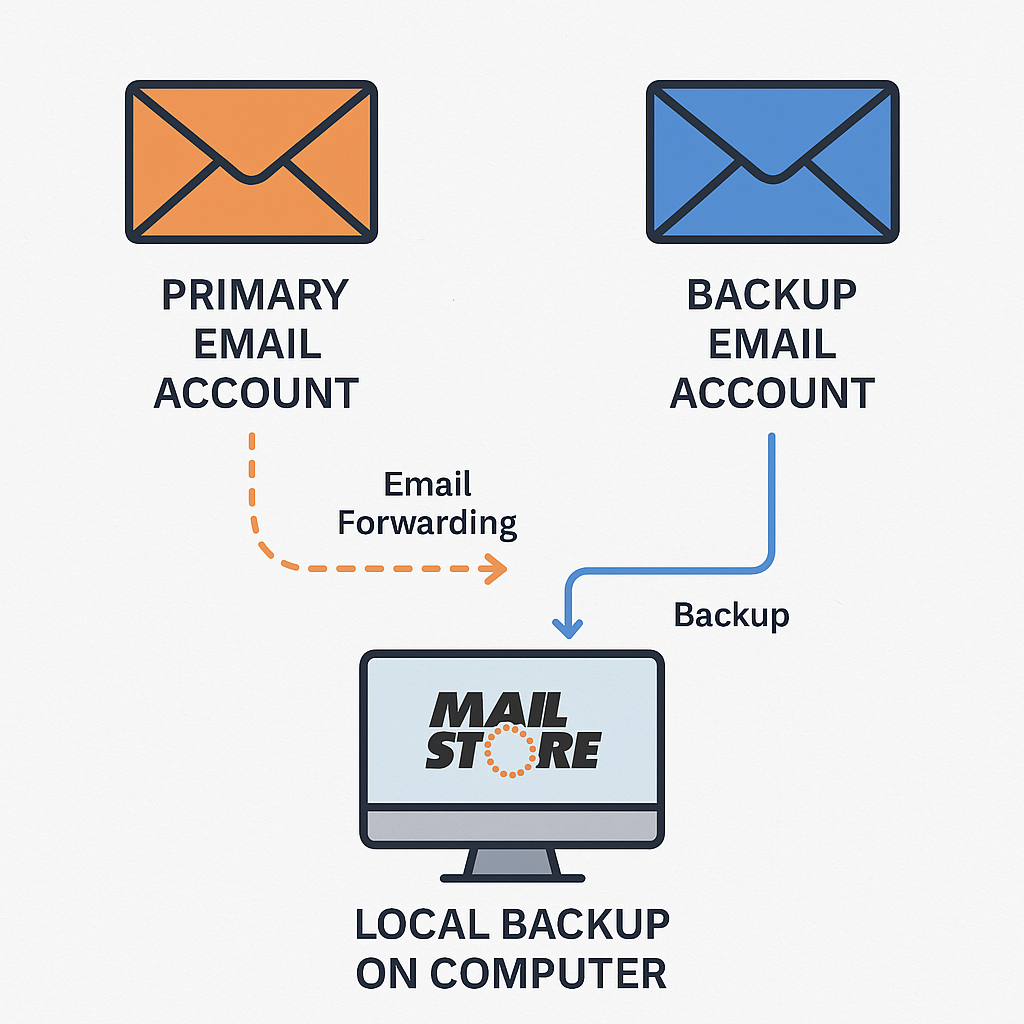
Core Architecture = Dual-Account Foundation
The picture illustrates a robust, multi-layered strategy for safeguarding personal email communications through redundancy, automation, and secure storage. It highlights the flow of data from a Primary Email Account, which forwards messages to a Backup Email Account on a different provider. From there, a local archive is maintained using MailStore, ensuring offline protection and long-term retention. By separating roles and diversifying access points, this setup minimizes the risk of data loss and ensures continuity even if one or more systems fail.
1. Primary & Secondary Email Accounts
– Primary Account: Your main daily-use email address
– Secondary Account: Independent backup on a different provider (e.g., if primary is Gmail, use
Outlook/ProtonMail)
– Critical: Use completely different passwords and security questions for each account
– Note: Consider choosing providers with strong privacy policies and good reputations for security and
uptime.
2. Multi-Factor Authentication (MFA) Implementation
– Enable MFA on both accounts using authenticator apps (Google Authenticator, Authy ect.
– Avoid SMS-based 2FA due to SIM swapping vulnerabilities
– Distribute authenticators across multiple devices to prevent single points of failure
– Generate and securely store backup codes for both accounts
– Review and revoke MFA devices periodically, especially after device loss or personnel changes.
3. Email Forwarding Configuration
– Primary -> Secondary: Forward all incoming emails to backup account
– Selective forwarding: Consider forwarding only critical emails to avoid storage issues
– Regular monitoring: Check forwarding rules monthly for unauthorized changes
– Alternative: Use email client rules instead of server-side forwarding for better control
– Audit logs: Enable and periodically review login and forwarding change logs if available.
4. Local Email Archiving (Recommended)
– Tools: MailStore Home (Windows), Gmvault (cross-platform), or Thunderbird with local storage
– Schedule: Automated weekly full backups with daily incremental updates
– Storage: Encrypted external drive or NAS with offline capability
– Retention: Keep local archives for at least 2-3 years beyond account deletion
– Testing: Regularly verify archive integrity and restoration procedures
– Backup redundancy: Maintain copies of archives in geographically separate locations if possible.
5. Password Management & Account
– Password Manager: Use reputable solutions (1Password, Bitwarden, LastPass)
– Unique passwords: Never reuse passwords between email accounts
– Password rotation: Update passwords every 6-12 months or after security incidents
– Security monitoring: Enable login alerts and review account activity logs monthly
– Phishing awareness: Train yourself and team members to recognize phishing attempts and suspicious
links.
6. Additional Security Layers
– App-specific passwords: Use for email clients instead of main account passwords
– Email encryption: Consider ProtonMail or similar for sensitive communications
– Regular security audits: Review connected apps, forwarding rules, and access permissions quarterly
– Incident response plan: Document steps to take if either account is compromised
– Use VPNs when accessing email over public or untrusted networks to protect data in transit.
7. Account Recovery Planning
– Recovery contacts: Set up trusted contacts on both accounts
– Recovery methods: Multiple recovery options (backup email, phone, security questions)
– Documentation: Maintain secure record of account details, recovery codes, and procedures
– Testing: Practice account recovery procedures annually
– Consider legal documentation for account access in case of emergencies or incapacitation.
8. Monitoring & Maintenance
– Monthly checks: Verify forwarding rules, review security logs, test backup systems
– Quarterly reviews: Update passwords, review connected services, audit permissions
– Annual testing: Full disaster recovery test including archive restoration
– Automate reminders for these tasks to maintain discipline.
9 Critical Success Factors
1. Provider Diversity: Use different email providers to avoid single-provider risks
2. Geographic Distribution: Consider providers in different jurisdictions for added protection
3. Regular Testing: Monthly verification of all backup systems and procedures
4. Documentation: Maintain updated procedures and contact information
5. Access Control: Limit forwarding and backup system access to essential personnel only
6. Continuous Improvement: Stay updated on evolving threats and patch security gaps promptly.
10 Emergency Response Protocol
If Primary Account Compromised:
1. Immediately change secondary account password
2. Disable forwarding rules from primary account
3. Notify contacts using secondary account
4. Begin local archive restoration process
5. Report incident to primary email provider
6. Review and revoke any connected third-party app access
If Secondary Account Compromised:
1. Disable forwarding to secondary account
2. Change primary account password as precaution
3. Restore from local archives if necessary
4. Establish new secondary account on different provider
5. Review and update all associated credentials and security settings
This multi-layered approach ensures email continuity even if multiple systems fail simultaneously.